Users
Kraken CI has user authentication and authorizations. Before a user starts using the system, he/she must log in to the system. Still, a user does not have access to all resources. Access is limited by roles that are assigned to a user.
Managing Users
Managing users is only available to admin user and users with
superadmin role. The user management page can be accessed via the
Configuration menu at the top right, then Users position and
again Users menu item.
Clicking it leads to the users management page.
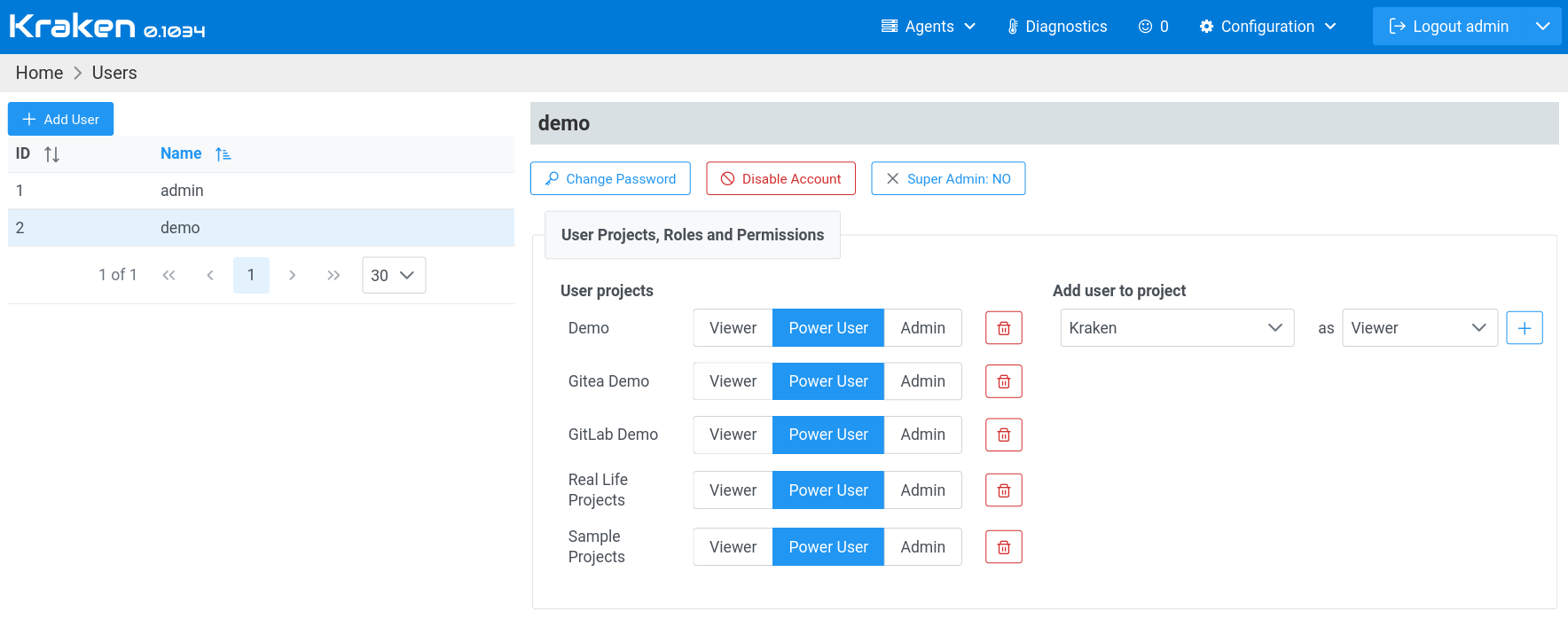
On the left is an Add User button and a table with users.
Selecting a user in this table shows its details in the right panel.
This user panel allows for changing a user password, disabling a user,
assigning superadmin role and assigning one of the three predefined
roles in a selected project.
Adding a User
Clicking the Add User button opens a dialog that allows for entering a
user name and a password.
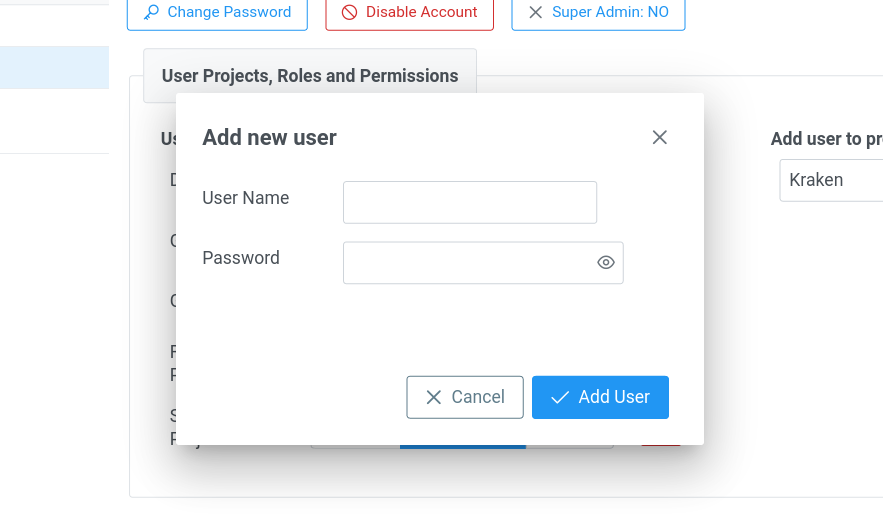
When adding is accepted by the Add User button in the dialog box,
then it is shown in the users table. Selecting the user shows its
details in the user panel on the right side.
Basic User Options
In the user panel, it is possible to change a user password by clicking
Change Password button.
It is also possible to disable a user account. A disabled user cannot login into the system and cannot do any operation if it is already logged in to the system.
User Roles
There are two kinds of roles:
- global role
superadmin - three predefined roles per project:
Viewer,Power UserandAdmin
superadmin role allows for all available operations in the system.
The per-project roles give some rights only to a given project. The rights are grnted by the roles:
Viewer- allows for viewing data only: browsing branches, their flows, results, etc.Power User- extendsViewerrole by allowing for triggering actions like: run a flow, rerun a job, define new stage, etc.Admin- extendsPower Userrole by allowing for e.g. deleting a branch or a project, managing project secrets.
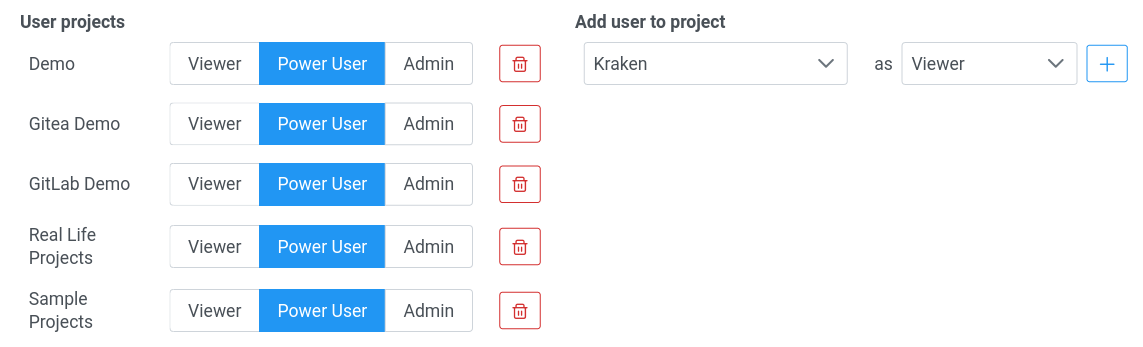
The selected user may be assigned to a given project with a given role. Later this role can be changed by clicking a role for a given project. At the end, it is possible to remove a user from a particular project.
Identity Providers
By default, user authentication is happening locally in the Kraken server. Still, it is possible to provide an external source of users and means for authentication by so-called Identity Providers. This also allows setting up Single Sign-On (SSO) scheme ie. users may sign in once in a central authentication system and then use it for authentication in other systems and services.
To set this up, go to the Configuration menu at the top right, then
Users position and Identity Providers menu item.
This leads to the Settings web page with the Identity Providers tab.
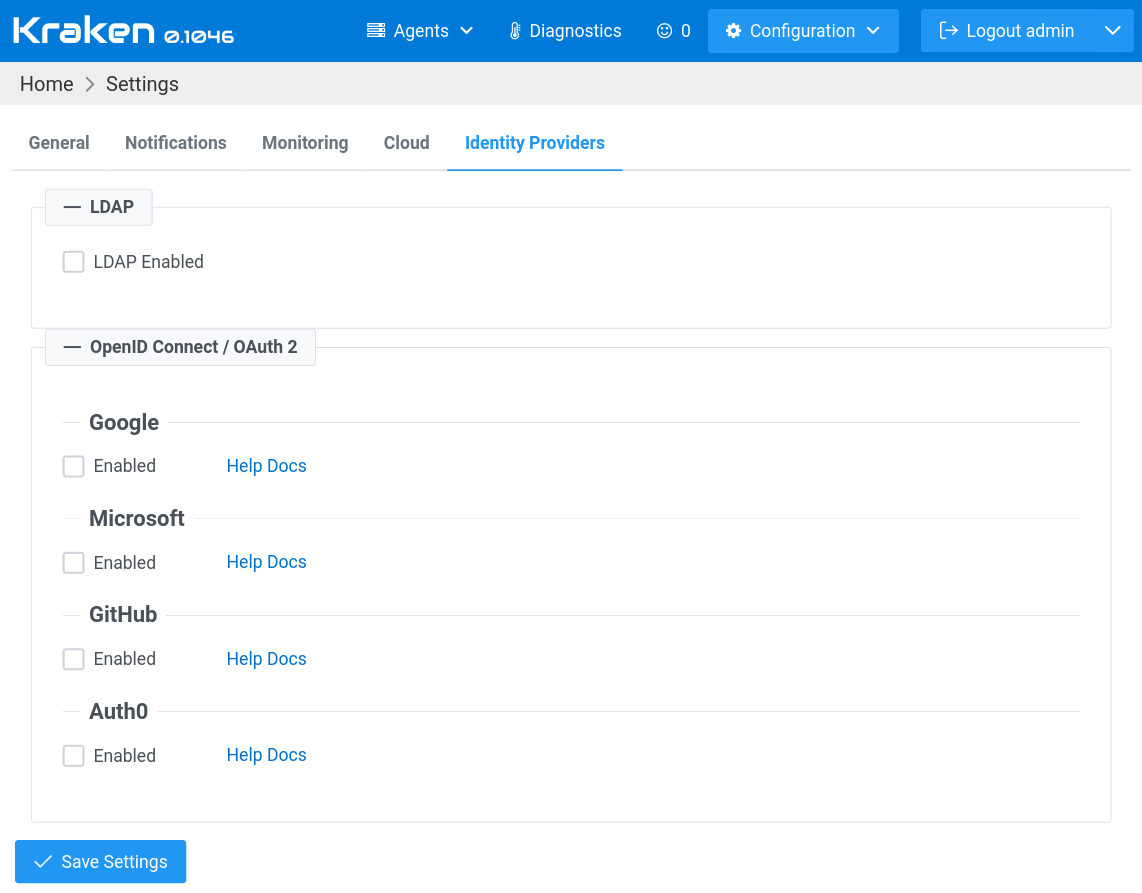
On this tab, there are 2 sections available:
- LDAP
- OpenID Connect / OAuth 2
LDAP
The source of users' identity is an LDAP server, which is used for users' authenticating. The login page is the same for local users in Kraken Web UI. Kraken Server authenticates users using credentials provided by them on this login page. Kraken Server connects to LDAP Server and checks if a user is present in LDAP server and his/her password is correct.
To perform this operation, Kraken Server needs a few settings that will allow Kraken Server to talk to LDAP Server. These settings need to be provided in the following form:
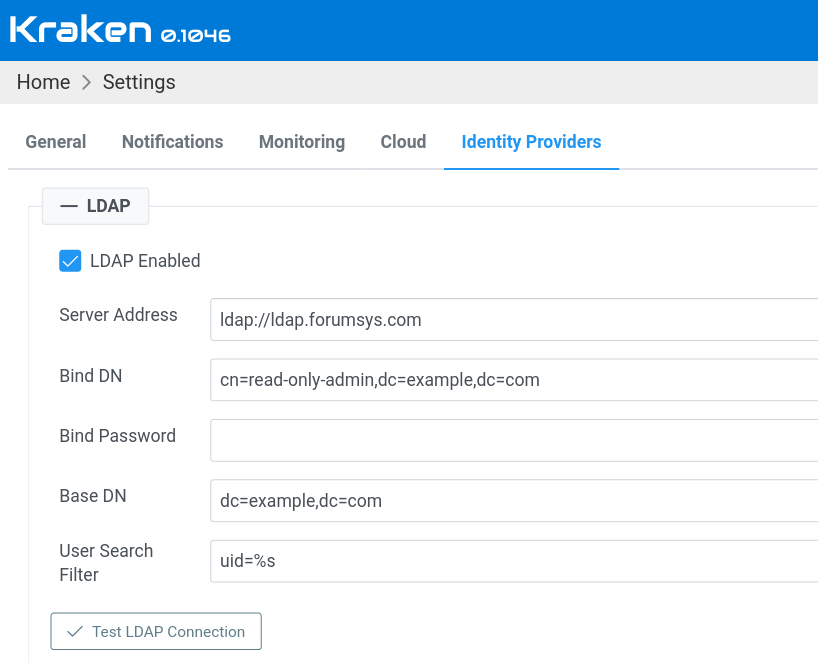
Server Address is an apparent field. Bind DN (Distinguished Name)
and Bind Password are used to authenticate Kraken Server to LDAP
Server. They are needed to connect to LDAP Server. Base DN is a
subtree in LDAP tree where users are looked for. User Search Filter is an LDAP query expression used to look for users in
Base DN subtree. In %s placeholder is inserted a user's username
that is provided by a user on the login page.
After saving the settings using the Save Settings button on the
bottom of the page, it is possible to check if configured parameters
are correct and if they allow to establish a connection to LDAP
Server. For that purpose, the Test LDAP Connection button should be
used.
OpenID Connect and OAuth
In the case of OpenID Connect and OAuth, the source of users' identity is OAuth Authorization Server. In this case, Kraken Web UI redirects to an external login page hosted on Authorization Server. A user enters his/her credentials to this server and then this server redirects the browser back to Kraken Web UI, providing a user token. Kraken Server is validating this token against the Authorization Server to confirm that this is a valid user. If all is ok, a user is allowed by Kraken Server to enter Kraken Web UI.
To perform this operation, Kraken Server needs a few settings that will allow Kraken Server to talk to OAuth Authorization Server. Kraken supports several providers of OAuth Authorization Servers. They are Google, Microsoft, GitHub and Auth0. The settings for these providers may be provided in the following forms:
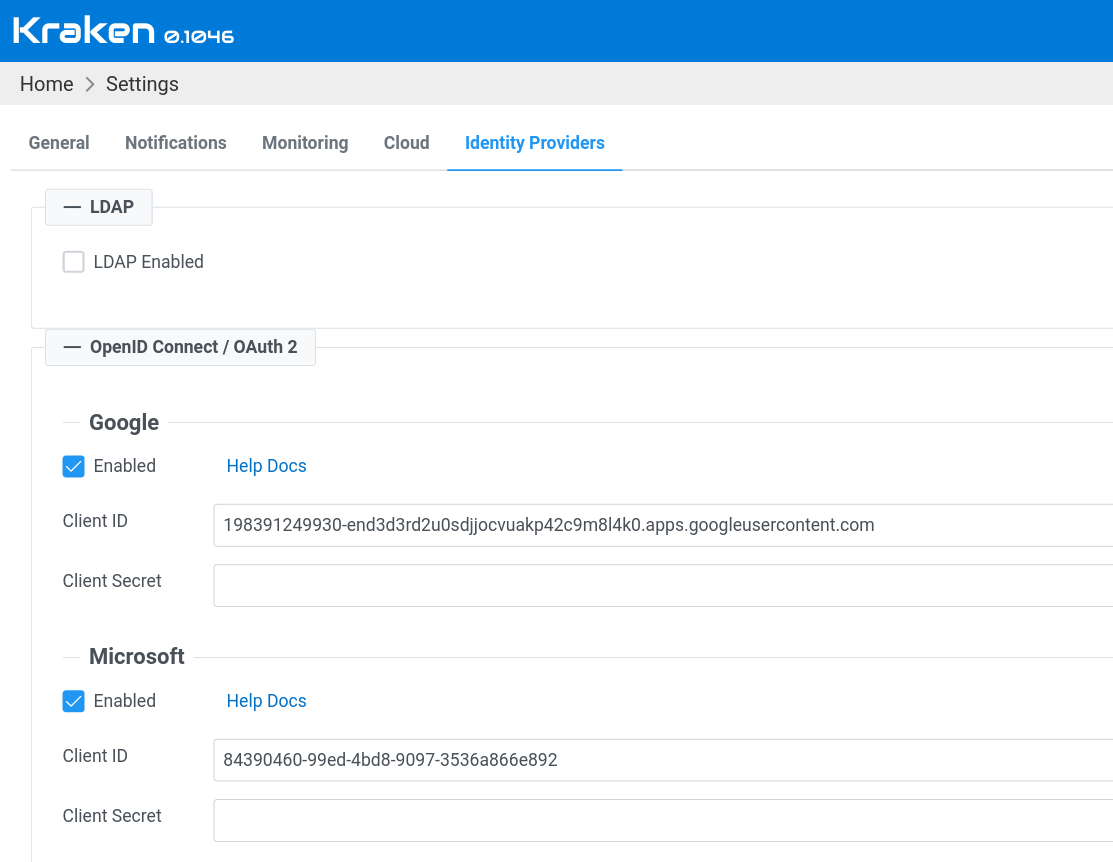
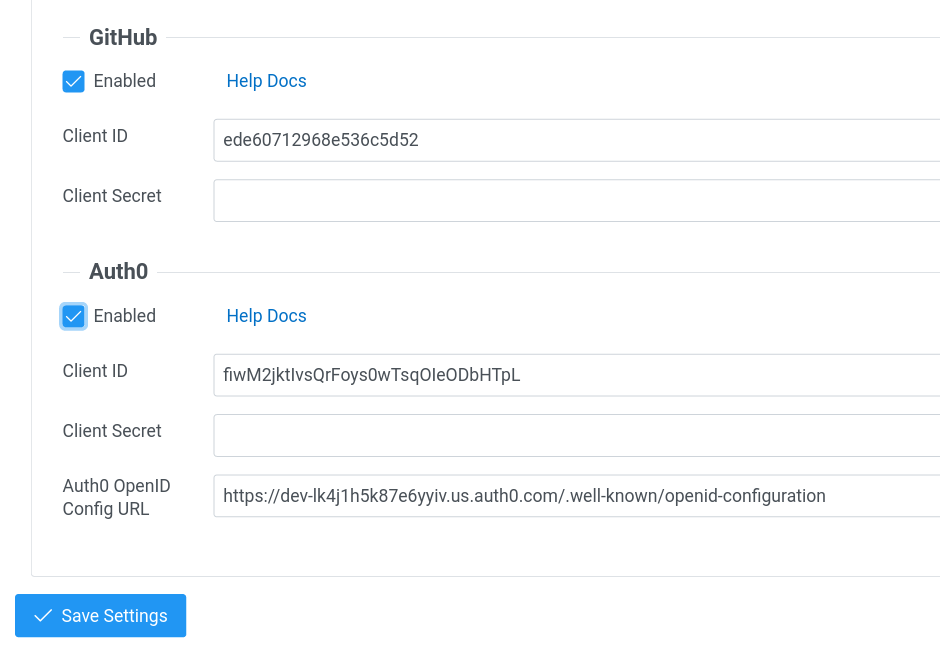
In each case, Client ID and Client Secret are needed. In the
case of Auth0, the OpenID Config URL is also required, which is
specific per organization.
More details on how to set up OpenID Connect and OAuth of the providers side can be found in the following documentation pages: